1. ICN-enabled IEEE 802.11 Wireless Access Points as Nano Data Centers.
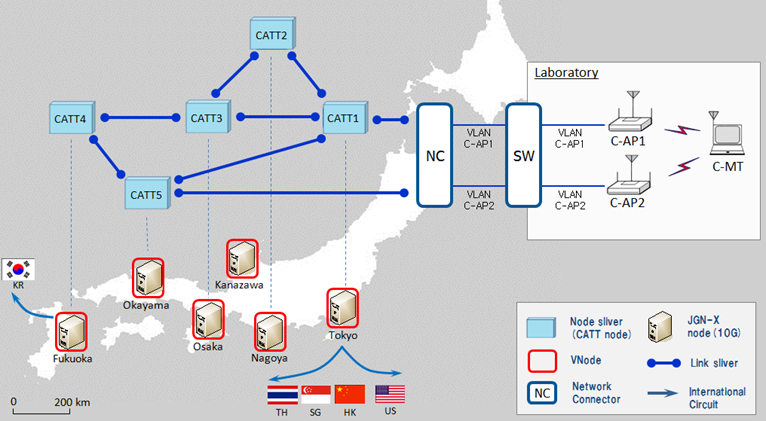 ICN has attracted much attention of network research community due to its paradigm shift in the network from end host to
information. In this paradigm, a perpetual connectivity is no longer required between end-to-end hosts, which enables ICN to
support mobility as the norm. More specifically, ICN communicates using the name of data object, which eliminates
the need for end terminals to resolve the location of the data based on its name. This simplifies mobility management for
the end hosts, especially when the data or the host holding the data is relocated during the communication. Moreover,
the name based communication, which is the essence of ICN, enables individual ICN nodes to be aware of user requests as
well as the corresponding responses so that any ICN elements can host data objects and deliver them to users on requests,
which functions as an independent content provider. In the light of the observations, we extend an ICN architecture
named CATT (Cache Aware Target idenTification), to mobile environment to design IEEE 802.11 wireless access points (APs)
with CATT so that network operators can use it as a nano data center which can be complementing existing data centers.
ICN has attracted much attention of network research community due to its paradigm shift in the network from end host to
information. In this paradigm, a perpetual connectivity is no longer required between end-to-end hosts, which enables ICN to
support mobility as the norm. More specifically, ICN communicates using the name of data object, which eliminates
the need for end terminals to resolve the location of the data based on its name. This simplifies mobility management for
the end hosts, especially when the data or the host holding the data is relocated during the communication. Moreover,
the name based communication, which is the essence of ICN, enables individual ICN nodes to be aware of user requests as
well as the corresponding responses so that any ICN elements can host data objects and deliver them to users on requests,
which functions as an independent content provider. In the light of the observations, we extend an ICN architecture
named CATT (Cache Aware Target idenTification), to mobile environment to design IEEE 802.11 wireless access points (APs)
with CATT so that network operators can use it as a nano data center which can be complementing existing data centers.
2. CATT: Potential Based Routing with Content Caching.
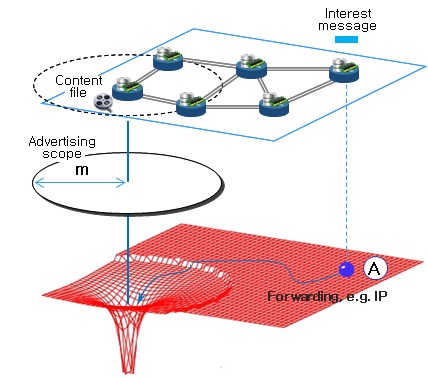 Since the Internet was initially designed as a connection oriented communication network, its role
has been changed to a content oriented data sharing network. This new paradigm requires a major
transformation of the current Internet architecture, which leads to the birth of Information
Centric Networking (ICN) concept in today's Internet. In this project we design an ICN
architecture named the Cache Aware Target idenTification (CATT) and introduce the architecture by
focusing on two of its major components, namely routing and content caching. For each component of
the CATT, Potential Based Routing (PBR) and topology aware caching policy are proposed
respectively. Due to the synergy effect of both
components, the CATT provides an efficient solution of content dissemination in ICN environment.
Since the Internet was initially designed as a connection oriented communication network, its role
has been changed to a content oriented data sharing network. This new paradigm requires a major
transformation of the current Internet architecture, which leads to the birth of Information
Centric Networking (ICN) concept in today's Internet. In this project we design an ICN
architecture named the Cache Aware Target idenTification (CATT) and introduce the architecture by
focusing on two of its major components, namely routing and content caching. For each component of
the CATT, Potential Based Routing (PBR) and topology aware caching policy are proposed
respectively. Due to the synergy effect of both
components, the CATT provides an efficient solution of content dissemination in ICN environment.
3. Development of the self-organizing algorithm to construct a short tail power law topology for P2P networks.
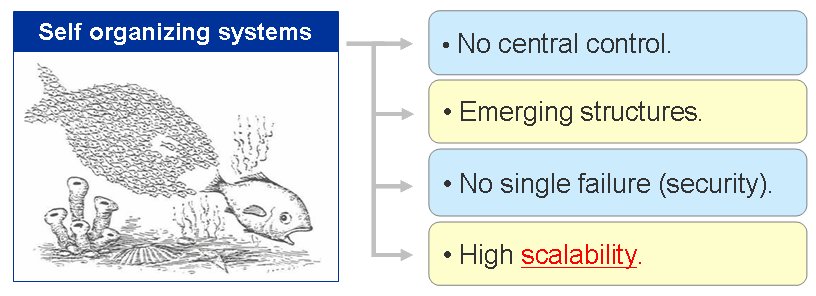 A power law topology is known to provide the best searching effiency as well as high robustness against
random failures on peers. However, there are also some known problems in use of a power law topology
for P2P networks. For instance, conventional algorithms to construct a power law topology require a
global view of the network, which is practically impossible as the size of network increases (scalability
issue), and moreover such information about the network can be used maliciously (security issue). In
addition, a very few of nodes in a power law topology suffer from high degrees/traffic (fairness issue).
A power law topology is known to provide the best searching effiency as well as high robustness against
random failures on peers. However, there are also some known problems in use of a power law topology
for P2P networks. For instance, conventional algorithms to construct a power law topology require a
global view of the network, which is practically impossible as the size of network increases (scalability
issue), and moreover such information about the network can be used maliciously (security issue). In
addition, a very few of nodes in a power law topology suffer from high degrees/traffic (fairness issue).
To tackle the problems, in the project we developed a self organizing algorithm to construct a short tail
power law topology for P2P networks. The self organizing mechanism solves the problems of scalability as
well as security issues appeared in conventional algorithms, and adopting the mechanism of constructing
a short tail power law topology overcomes the issue of fairness. The emergence of a short tail power law
topology through the proposed method is verifed numerically, and the numerical results are confirmed by
analytical result. Moreover, the performances of constructed short tail power law topologies are evaluated
in terms of searching effiency and robustness that are highly required for P2P networks.
4. Development of the self-organizing algorithm for the topological transformation of Peer-to-Peer (P2P) networks.
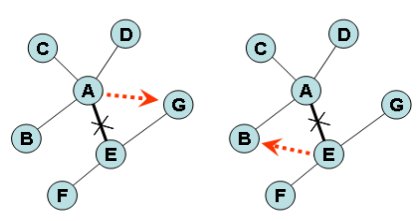 Although, conventional approaches can construct a small diameter topology of which P2P networks can
take advantage to achieve high search efficiency, some extreme cases such as disastrous multiple failures
of peers may distort its structure severely so that inherent topological advantages may be disappeared.
In such a case, some mechanisms are required to restore the distorted topological structure.
Although, conventional approaches can construct a small diameter topology of which P2P networks can
take advantage to achieve high search efficiency, some extreme cases such as disastrous multiple failures
of peers may distort its structure severely so that inherent topological advantages may be disappeared.
In such a case, some mechanisms are required to restore the distorted topological structure.
For this reason, in this project we developed a rewiring method to transform a network topology into
a small diameter and highly clustered network topology. The proposed method can be implemented in a
self organizing manner which means that individual peers interact directly with each other in a distributed
fashion without any externally or centrally dedicated control unit. Additionally, we demonstrated how a
truncated power law topology can be constructed through the proposed rewiring method. The truncated
power law topology solves one known problem in a general power law topology that a few hub nodes
suffer from high traffic load which is not desirable phenomenon for P2P networks.
5. Designing a responsive dynamic system for logical topology control.
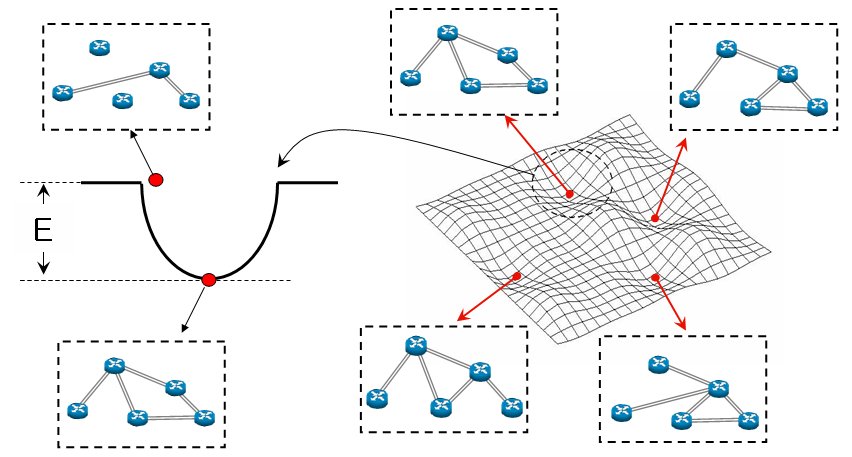 There has been an attempt to use a dynamic model called an attractor selection method for the control
of a logical topology. While the conventional approach focused on the use of the stochastic behavior of
the model, the deterministic part of the model, which can be considered as an attractor network, was
relatively ignored.
There has been an attempt to use a dynamic model called an attractor selection method for the control
of a logical topology. While the conventional approach focused on the use of the stochastic behavior of
the model, the deterministic part of the model, which can be considered as an attractor network, was
relatively ignored.
In this project we make use of the deterministic part of the model called an attractor network to
control the topological structure of a logical network. There are two advantages using the attractor
network model. Firstly, a lyapunov function is defined in the model. Thus, when a system state becomes
unstable due to some disturbances over the system, the dynamic system always improves its stability
through the dynamic process. In other words, the dynamic evolution guarantees that the system evolves
into a stable system state. Secondly, the evolution speed of the dynamic system can be improved by
realizing the model on electronic circuit, possibly on a VLSI (Very large-scale integration) circuit with a
parallel-distributed process.
6. Traffic Matrix estimation: deterministic approach.
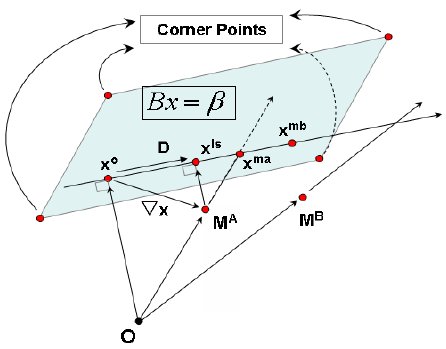 Traffic Matrix estmation problem is formulated as a non-linear optimization problem based on the generalized Kruithof approach and then the affine scaling method is used to solve the optimization problem. We have proposed a strategy to accelerate the rate of convergence of the affine scaling method using a geometric analysis of the problem. The strategy involves finding good starting points and a search directions since the choice of the feasible starting point and the searching direction affect the convergence speed of the interior point algorithm.
Traffic Matrix estmation problem is formulated as a non-linear optimization problem based on the generalized Kruithof approach and then the affine scaling method is used to solve the optimization problem. We have proposed a strategy to accelerate the rate of convergence of the affine scaling method using a geometric analysis of the problem. The strategy involves finding good starting points and a search directions since the choice of the feasible starting point and the searching direction affect the convergence speed of the interior point algorithm.
7. Traffic Matrix estimation: statistical approach.
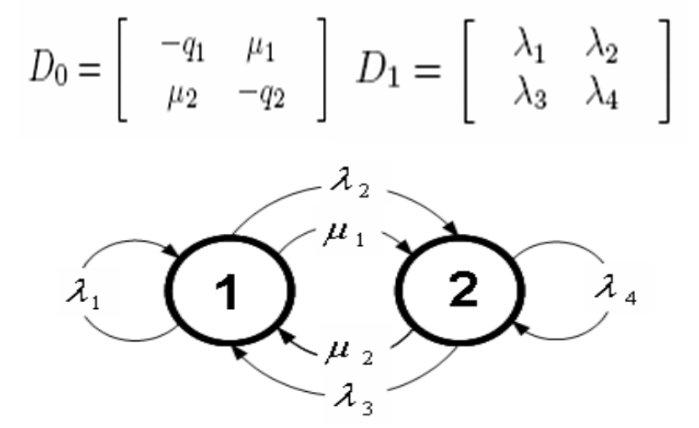 We proposed a new statistical approach for traffic matrix estimation, which incorporates a traffic descriptor, Markovian Arrival Process of order two (MAP2), that allows the burstiness and correlation structure of IP traffic to be modelled. The proposed method solves the traffic matrix estimation problem by dividing it into two main subproblems: 1) First, from a multiple set of link counts obtainable from a consecutive set of Simple Network Management Protocol (SNMP) measurements and a given routing matrix, obtain a series of traffic matrices by applying a standard deterministic approach. The components of these matrices represent estimates of the volumes of flows being exchanged between all pairs of nodes at the respective measurement points and they form a stochastic counting process. 2) Then, a Markovian Arrival Process of order two (MAP-2) is applied to model the counting processes formed from this series of estimated traffic matrices.
We proposed a new statistical approach for traffic matrix estimation, which incorporates a traffic descriptor, Markovian Arrival Process of order two (MAP2), that allows the burstiness and correlation structure of IP traffic to be modelled. The proposed method solves the traffic matrix estimation problem by dividing it into two main subproblems: 1) First, from a multiple set of link counts obtainable from a consecutive set of Simple Network Management Protocol (SNMP) measurements and a given routing matrix, obtain a series of traffic matrices by applying a standard deterministic approach. The components of these matrices represent estimates of the volumes of flows being exchanged between all pairs of nodes at the respective measurement points and they form a stochastic counting process. 2) Then, a Markovian Arrival Process of order two (MAP-2) is applied to model the counting processes formed from this series of estimated traffic matrices.
8. Traffic Matrix estimation: dynamic approach.
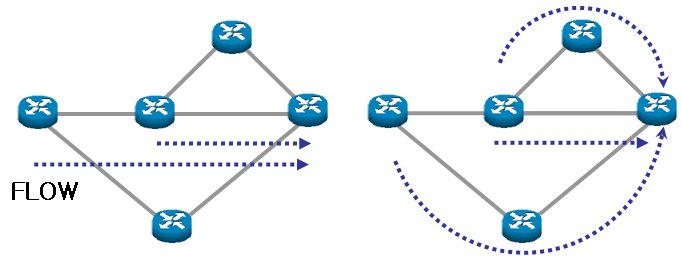 We proposed a new dynamic approach for TM estimation that formulates the weight changes problem as the LP based on the dual version of the multi-commodity flow problem. Since the proposed method takes advantage of an LP approach which is a mature field that provides many efficient and fast algorithms to solve large problems, it is computationally more efficient than the previously adopted heuristic search algorithms as well as enabling the setting of link load limits in the problem formulation so that the re-route traffic using a new weight set does not cause an overloaded network.
We proposed a new dynamic approach for TM estimation that formulates the weight changes problem as the LP based on the dual version of the multi-commodity flow problem. Since the proposed method takes advantage of an LP approach which is a mature field that provides many efficient and fast algorithms to solve large problems, it is computationally more efficient than the previously adopted heuristic search algorithms as well as enabling the setting of link load limits in the problem formulation so that the re-route traffic using a new weight set does not cause an overloaded network.